Blog
Most Wanted Security Technology for 2019: Security Analytics
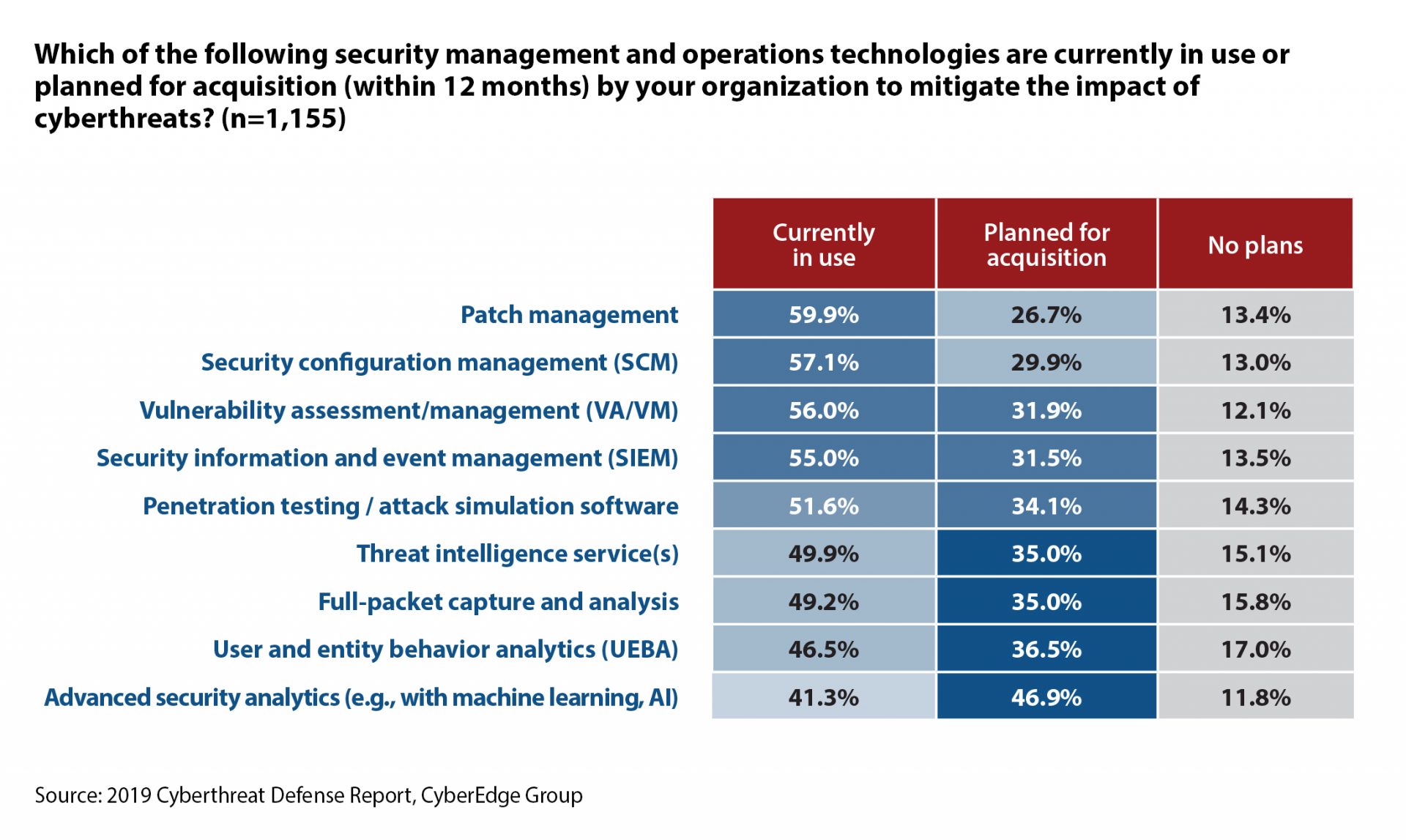
CyberEdge recently announced results from its sixth annual Cyberthreat Defense Report (CDR). This report harnesses perceptions of cyberthreats and IT security defenses from 1,200 security professionals across 17 countries and 19 industries. Click here to download your copy now.
Each year, we ask our research participants to identify those security technologies their respective organizations already have in place and those they plan to acquire in the coming year. We group together these technologies into five distinct segments:
- Network security
- Endpoint security
- Application and data security
- Security management and operations
- Identity and access management
Not only was security analytics the most sought-after technology in the security management and operations segment, with 47% of organizations planning investments in 2019, but it was also the highest rated security technology across all five segments!
A Primer on Security Analytics
If you’re not up to speed on what security analytics is all about, it’s the process of using data collection, aggregation, and analysis tools for security monitoring and threat detection. Modern security analytics products incorporate machine learning and/or artificial intelligence (AI) to help take the guesswork out of validating security alerts and minimizing the potential for false positives. Today’s security analytics products ingest a plethora of internal and external data, including:
- Network traffic
- Endpoint and user behavior data
- Identity and access management data
- Threat intelligence
- Geolocation
Enterprises are leveraging security analytics products to enable a variety of use cases, including:
- Hunting for advanced / unknown cyberthreats
- Detecting insider threats
- Identifying compromised accounts
- Detecting unauthorized data exfiltration
- Investigating security incidents
So, why is Security Analytics so hot?
This question is answered, in part, by a survey question we ask year after year – “What’s inhibiting your organization from adequately defending itself against cyberthreats?” Usually, it’s about ‘lack of skilled personnel’ or ‘low security awareness among employees.’ But this year, another cause bubbled to the top – ‘too much data to analyze.’
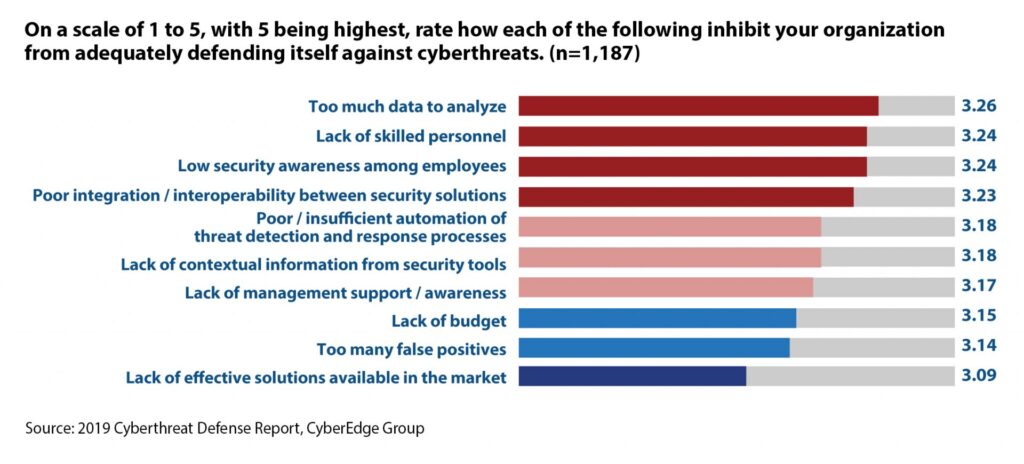
Security analytics and incident responders are inundated with data from a myriad of sources. It’s like listening to dozens of baby rattles going off, all at once, all day long. It’s incredibly challenging to turn raw data from disparate sources into actionable insights. Fortunately, advancements in machine learning and AI are helping security practitioners ‘cut through the noise’ so they can focus on what really matters.
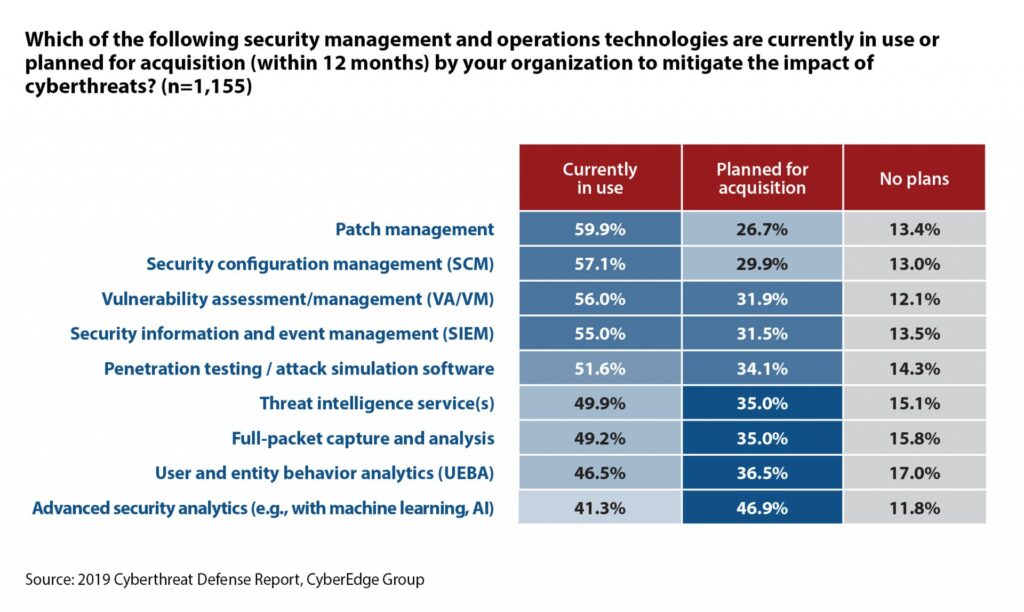
How is Security Analytics being deployed?
This question is also addressed by this year’s CDR. We asked our respondents how they’ve added, or are planning to add, security analytics capabilities to their cyberthreat defenses. Here’s what we learned:

Clearly, there’s no one method for deploying security analytics technology. Whether you’re augmenting your current SIEM, or relying on your SIEM vendor or MSSP partner to deliver security analytics capabilities, your organization will almost certainly see a return on your security analytics investment.
Download the 2019 CDR Report
Click here to download the full 50-page report. CyberEdge is grateful for its Platinum, Gold, and Silver sponsors, for without whom this report would not be possible:
- Platinum sponsors: Code42, DXC Technology, Gigamon, and Imperva
- Gold sponsors: Aqua Security, LookingGlass, Recorded Future, and StackRox
- Silver sponsors: Arctic Wolf, Bandura, CTERA, DisruptOps, Edgeworx Solutions, and Illusive Networks