
Blog
“Hotspots” from 2015 Cyberthreat Defense Report – Part 1
CyberEdge Group’s second annual Cyberthreat Defense Report surfaced a number of emerging areas of interest that we believe will warrant close attention from IT security teams in 2015 and beyond. Of course, if enterprises are paying close attention to these trends then so to should the marketing and product management teams at IT security solution providers. The plan is to reveal two of these emerging hotspots now, while reserving another pair for a subsequent post.
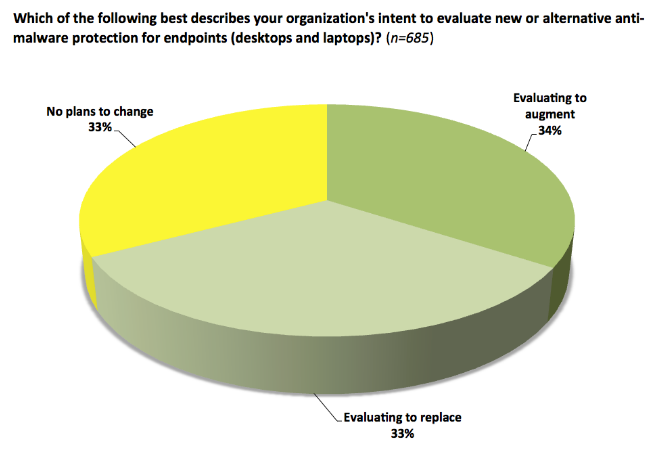
Next-generation endpoint defenses. More than two-thirds of our survey respondents indicated their organizations are looking to replace or augment current endpoint protection tools. The issue isn’t that traditional, signature-based endpoint solutions are broken; rather, it’s that what they do is no longer sufficient (primarily detect known malware). Fortunately, the market is responding with a new wave of innovation for endpoint defenses.

Next-generation solutions that deserve consideration for augmenting legacy endpoint security tools fall into several evolving categories:
- Host-intrusion prevention 2.0 – where system-level “traps” and “check points” are set/monitored to detect the relatively modest set of exploit mechanisms most malware relies upon;
- Containerization/micro-virtualization – where isolated, short-duration “workspaces” shield the endpoint from contracted infections and reset to a known clean state upon completion of each user session;
- Real-time file classification and execution control – where advanced machine learning algorithms make real-time permit/deny decisions regarding file execution; and,
- Big data correlation – where advanced endpoint instrumentation is coupled with an out-of-band analysis engine.
The evolution of cyberthreat intelligence services. Basic threat intelligence services are far from useless. Feeds that deliver malware signatures, URL reputation data, and intrusion indicators directly and immediately improve the effectiveness of commonly deployed threat detection and prevention technologies. Other, mid-level feeds that include basic information on the prevalence, sources, and targets of malware and attack activities help expose patterns and may even reveal how to remediate compromised systems. However, even greater value can be derived from the still-coalescing top end of this rapidly growing market segment. The high-level feeds delivered in this case are fully customized to individual customers’ requirements and include forward-looking analysis of threats, actors, and methods that can be used not only for tactical purposes – such as immediate adjustment of configured countermeasures – but also to inform an organization’s longer term security strategy.
For further insights on these and other trends – or to develop compelling marketing content that capitalizes on them – just give us a shout. We’re always eager to help!


