Blog
2019 Cyberthreat Defense Report – Spotlight on Container Security Platforms
Every year when we publish the Cyberthreat Defense Report (2019 edition here), we highlight a handful of emerging (or significantly evolving) areas/technologies we believe have the potential to substantially enhance an organization’s ability to defend against current and future generations of cyberthreats. This post covers one on of these emerging hotspots: Container Security Platforms.
As the initial wave(s) of containerized applications transition from the Dev/Test environment into production, enterprises will need to take a more strategic approach to container security. Continuing to rely on tactical, piecemeal efforts featuring too-great emphasis on vulnerability scanning will only erode many of the benefits containers are meant to deliver, such as easier/quicker application revisions, more-efficient resource utilization, and superior scalability.
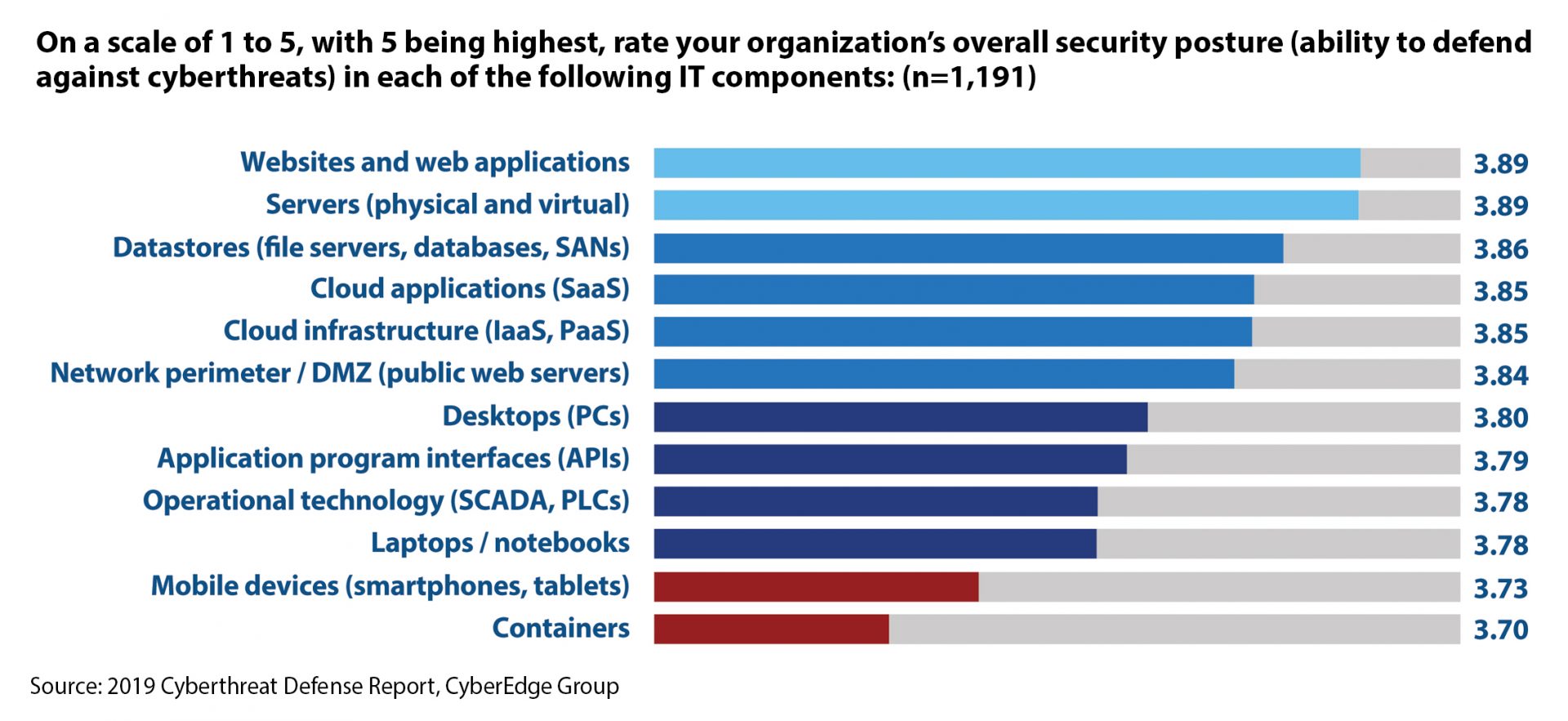
Don’t believe me? Then how about 1,200 of your peers – who identified application containers as being the part of their organization’s IT infrastructure with the weakest security posture?
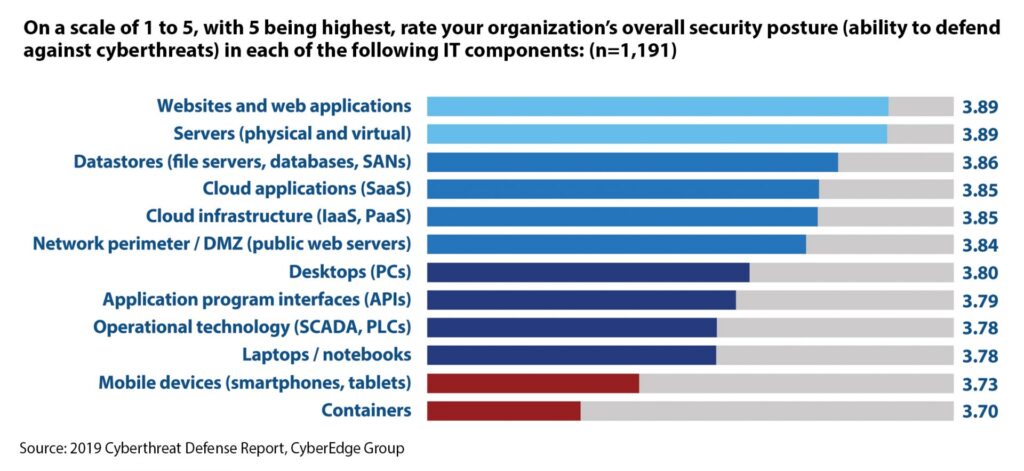
For organizations in such a position, container security platforms (CSPs) are a promising option that warrants close consideration. The goal of this rapidly maturing class of offerings is to provide the full set of security functionality that collaborating DevOps and security teams will need. This functionality accounts not only for all the key components of a containerized environment (images, containers, hosts, registries, and orchestrator) wherever they reside (on-premise or in the cloud), but also for each phase of the container lifecycle (i.e., build, deploy/ship, run).
As such, table stakes for a CSP include:
- Multi-phase vulnerability scanning and security configuration management
- Secrets management
- Automatic network segmentation / least-privilege access control (also known as container firewalling)
- Runtime monitoring for anomalous behavior (with configurable response actions)
- Policy and compliance auditing/reporting
- Out-of-the-box integration with all common CI/CD tooling
Evaluators intent on getting the most for their money, however, should also look for these next-level capabilities:
- Context-based prioritization of all vulnerability and configuration findings
- Threat/anomaly detection that automatically accounts for changing application behavior
- Continuous posture improvement through automated, cross-phase sharing of security information
If you have different/additional ideas, then please chime in. And, as always, if you’d like to engage in further discussion – or are looking for help marketing related solutions – just give us a shout. We’re here to help!