Blog
Next Steps for Application Security – Part 1
Every year when we publish the Cyberthreat Defense Report (2018 edition here), we highlight a handful of emerging (or significantly evolving) areas/technologies we believe have the potential to substantially enhance an organization’s ability to defend against current and future generations of cyberthreats. This time around, two of our showcased items relate to the white-hot discipline of application security: DevSecOps tools (covered in this post), and API gateways (featured in part 2).
Forgive us for the gross oversimplification, but fundamentally DevOps is all about harmonizing and de-serializing the efforts of software development, QA, and operations personnel to speed the delivery (and ideally improve the quality) of new apps, features, and fixes. DevSecOps, then, brings security into the fold, too. If all goes well, the net result is applications that are faster to market, better, cheaper, and more secure than ever before. Sounds great – I’ll take two servings please!
Of course, getting started on a DevOps/DevSecOps path is no small endeavor. The organizational (e.g., re-alignment) issues alone can be a substantial hurdle. Enterprises that manage the initial transformation then face the question of how best to begin bringing security into the mix. Our suggestion is to go after some low-hanging fruit. Ever the fans of doing more to reduce one’s attack surface, we recommend starting out with investments in application security testing (ideally, a combination of both the static and dynamic varieties) and open source vulnerability management tools.
While the former is instrumental to removing security defects from custom-developed code, the latter does much the same for the plethora of open source components that pervade today’s code bases. One further suggestion: do everything you can to automate the use of these tools, as well as the response activities that (should) follow whenever a defect is found; otherwise, you won’t truly be doing DevSecOps!
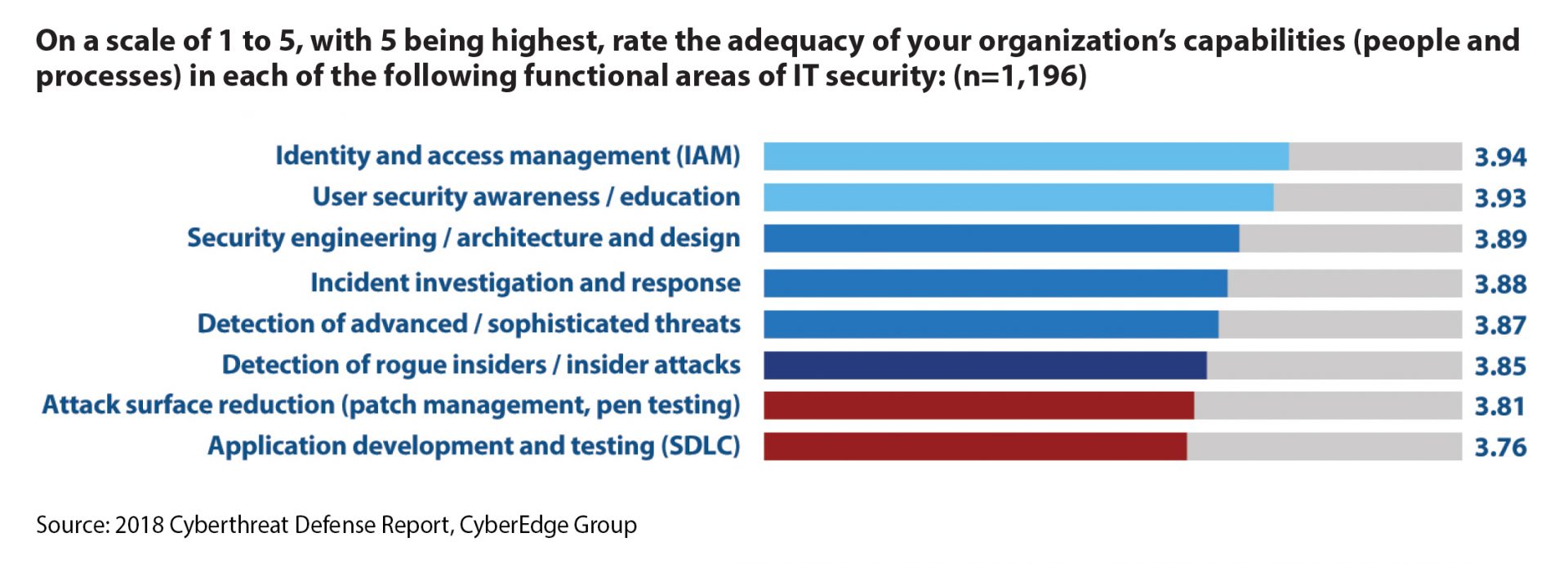
So that’s our quick (and dirty) plan for getting started with DevSecOps. We think it makes great sense, especially given the 2018 Cyberthreat Defense Report findings of app dev/testing and attack surface reduction being the two IT security processes our respondents struggle with the most.
 If you have different/additional ideas, then by all means, please sound off. And, as always, if you’d like to engage in further discussion – or are looking for help marketing related solutions – just give us a shout. We’re here to help!
If you have different/additional ideas, then by all means, please sound off. And, as always, if you’d like to engage in further discussion – or are looking for help marketing related solutions – just give us a shout. We’re here to help!