Blog
Insights and Observations from the 2014 Verizon Data Breach Investigations Report
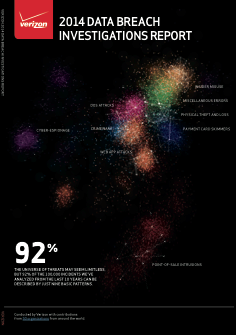
 Like its predecessors, the 2014 Verizon Data Breach Investigations Report (DBIR) is a treasure trove of real-world information about the cyberthreat landscape. A big change for this year’s report has to do with how the material is organized. In particular, Verizon has subsumed its signature approach of examining actors, actions, assets, and timelines under a higher-layer categorization of nine basic patterns that it has determined represent the vast majority (92%) of incidents encountered over the last 10 years. These patterns are:
Like its predecessors, the 2014 Verizon Data Breach Investigations Report (DBIR) is a treasure trove of real-world information about the cyberthreat landscape. A big change for this year’s report has to do with how the material is organized. In particular, Verizon has subsumed its signature approach of examining actors, actions, assets, and timelines under a higher-layer categorization of nine basic patterns that it has determined represent the vast majority (92%) of incidents encountered over the last 10 years. These patterns are:
- Point-of-Sale (PoS) intrusions
- Web Application Attacks
- Insider Misuse
- Physical Theft/Loss
- Miscellaneous Errors
- Crimeware
- Card Skimmers
- Denial of Service (DoS) Attacks
- Cyber-Espionage
Among the reasons Verizon gives for making this change is that the new approach “shows extreme promise as a way to drastically simplify the seemingly endless array of threats we must deal with to protect information assets.” That’s well said, and we couldn’t agree more that this method should help organizations focus their cyberthreat defense efforts – particularly when you consider that, on average, nearly three-quarters of the incidents for each of the 19 vertical industry classifications covered in the DBIR could be ascribed to just 3 of the 9 patterns.
Another major change is the inclusion of DoS attacks for the first time. While DoS attacks rarely lead to a breach involving exposure of sensitive data, they are nonetheless a significant threat for today’s organizations. In fact, this conclusion is validated by the Verizon data, which shows that only web attacks appear more frequently (12 times) than DoS attacks (9 times) among the top 3 incident patterns identified for each vertical industry.
A few other items that caught my attention on a first pass through the report are:
- That point-of-sale attacks are down, while cyber-espionage attacks are up – which also indicates a shift from payments and banking data being the target of choice to secrets and internal data more frequently being in the crosshairs;
- That the trend lines for time-to-comprise and time-to-discovery are continuing to diverge (in a bad way) – meaning that attackers are getting better/faster at what they do at a higher rate than defenders are improving their capabilities; and,
- The recommendation to “make your people your first line of defense” – which dovetails perfectly with the finding from our own 2014 Cyberthreat Defense Report that “low security awareness among employees” is the greatest factor inhibiting security teams from adequately defending their organizations against cyberthreats.
Kudos, once again, to Verizon for such a comprehensive and informative report. To download a copy of the 2014 Verizon DBIR, click here: http://www.verizonenterprise.com/DBIR/.